With OS X Yosemite,
Apple has included a number of Continuity features that improve the
integration between iOS and Mac devices. OS X Yosemite includes a
feature called Instant Hotspot which allows users to more easily use
their iPhone's wireless cellular data connection from their Mac or iPad.

With Instant Hotspot, there is no longer a need to enter a password to connect as security is handled through a common iCloud account. An iPhone can even be in sleep mode and allow your Mac to initiate Instant Hotspot, with no additional settings needing to be enabled aside from Wi-Fi and Bluetooth.
You need iOS 8.1 and OS X Yosemite in order to use Instant Hotspot. You also need to ensure that your data plan with your wireless carrier allows for internet hotspot capabilities. In the United States, AT&T, Verizon, and T-Mobile, allow phones to be used as hotspots with select data plans. Sprint offers mobile hotspot capabilities with a monthly add-on plan.
Also, make sure both your Mac and iPhone are logged into the same iCloud account, and check that your Mac supports Instant Hotspot. This can be done by clicking the symbol in the top left-hand side of the Menu bar, navigating to About This Mac, clicking on System Report and clicking on the Bluetooth listing. You should see information about whether your system is compatible with Instant Hotspot and Handoff.

After you ensure that you have a compatible Mac and data plan, follow the instructions below to turn on Instant Hotspot:
1. Turn on Wi-Fi on your iPhone (Settings -> Wi-Fi) and Mac (Menu Bar -> -> Turn Wi-Fi On.
-> Turn Wi-Fi On.
2. Turn on Bluetooth on your iPhone (Settings -> Bluetooth) and Mac (Menu Bar -> Apple -> System Preferences -> Bluetooth -> Turn Bluetooth On).
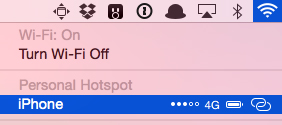
3. On your Mac, click the Wi-Fi symbol in the menu bar. A new "Personal Hotspot" heading now appears near the
top, and will be followed by the name of your iPhone. On the right side
of your iPhone's name, signal strength, network type, and available
battery life are displayed. Click on your device's name to begin using
it as an Instant Hotspot for your Mac.
in the menu bar. A new "Personal Hotspot" heading now appears near the
top, and will be followed by the name of your iPhone. On the right side
of your iPhone's name, signal strength, network type, and available
battery life are displayed. Click on your device's name to begin using
it as an Instant Hotspot for your Mac.
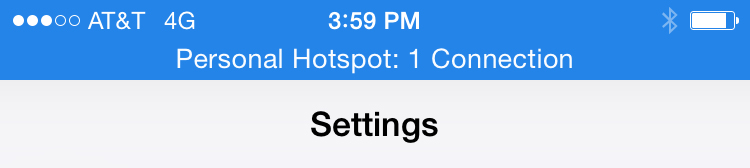
4. You may now begin using the Internet on your Mac with your iPhone acting as an Instant Hotspot. On the Mac, the Instant Hotspot connection between both devices is represented by a special icon that shows a link over the traditional Wi-Fi symbol. On the iPhone, the connection is represented by a blinking blue bar that shows that a Personal Hotspot is active.
When a tethered Mac or iPad switches to a Wi-Fi connection or is no longer connected to an iPhone, Instant Hotspot automatically turns off. This feature is designed to save battery on the iPhone, because tethering can use a significant amount of battery life.
While we had few issues with Instant Hotspot, several have had more inconsistent results. Several people have had to try logging out and back into iCloud on their devices, turning Wi-Fi off and then back on, or even rebooting their devices. These steps may help if you are having trouble turning using Instant Hotspot.

With Instant Hotspot, there is no longer a need to enter a password to connect as security is handled through a common iCloud account. An iPhone can even be in sleep mode and allow your Mac to initiate Instant Hotspot, with no additional settings needing to be enabled aside from Wi-Fi and Bluetooth.
Before you Start
You need iOS 8.1 and OS X Yosemite in order to use Instant Hotspot. You also need to ensure that your data plan with your wireless carrier allows for internet hotspot capabilities. In the United States, AT&T, Verizon, and T-Mobile, allow phones to be used as hotspots with select data plans. Sprint offers mobile hotspot capabilities with a monthly add-on plan.
Also, make sure both your Mac and iPhone are logged into the same iCloud account, and check that your Mac supports Instant Hotspot. This can be done by clicking the symbol in the top left-hand side of the Menu bar, navigating to About This Mac, clicking on System Report and clicking on the Bluetooth listing. You should see information about whether your system is compatible with Instant Hotspot and Handoff.
After you ensure that you have a compatible Mac and data plan, follow the instructions below to turn on Instant Hotspot:
Steps
1. Turn on Wi-Fi on your iPhone (Settings -> Wi-Fi) and Mac (Menu Bar ->
2. Turn on Bluetooth on your iPhone (Settings -> Bluetooth) and Mac (Menu Bar -> Apple -> System Preferences -> Bluetooth -> Turn Bluetooth On).

3. On your Mac, click the Wi-Fi symbol

4. You may now begin using the Internet on your Mac with your iPhone acting as an Instant Hotspot. On the Mac, the Instant Hotspot connection between both devices is represented by a special icon that shows a link over the traditional Wi-Fi symbol. On the iPhone, the connection is represented by a blinking blue bar that shows that a Personal Hotspot is active.
When a tethered Mac or iPad switches to a Wi-Fi connection or is no longer connected to an iPhone, Instant Hotspot automatically turns off. This feature is designed to save battery on the iPhone, because tethering can use a significant amount of battery life.
Troubleshooting
While we had few issues with Instant Hotspot, several have had more inconsistent results. Several people have had to try logging out and back into iCloud on their devices, turning Wi-Fi off and then back on, or even rebooting their devices. These steps may help if you are having trouble turning using Instant Hotspot.





















































